 WhisPeer Messaging App
WhisPeer Messaging App
End-to-End encrypted messaging using Signal Protocol implementation
 WhisPeer Messaging App
WhisPeer Messaging App
End-to-End encrypted messaging using Signal Protocol implementation
A secure, end-to-end encrypted chat application implemented with Java. The system implements a hybrid of Signal Protocol's Double Ratchet algorithm and X3DH key agreement protocol for maximum security and forward secrecy.
Messages are encrypted on sender's device and only decrypted on recipient's device using AES-256-GCM. Even server cannot read your messages.
Compromise of long-term keys doesn't compromise past messages. Each message uses a unique encryption key.
Two-way authentication using Diffie-Hellman key exchange with nonce-based challenge-response.
X3DH Key Agreement
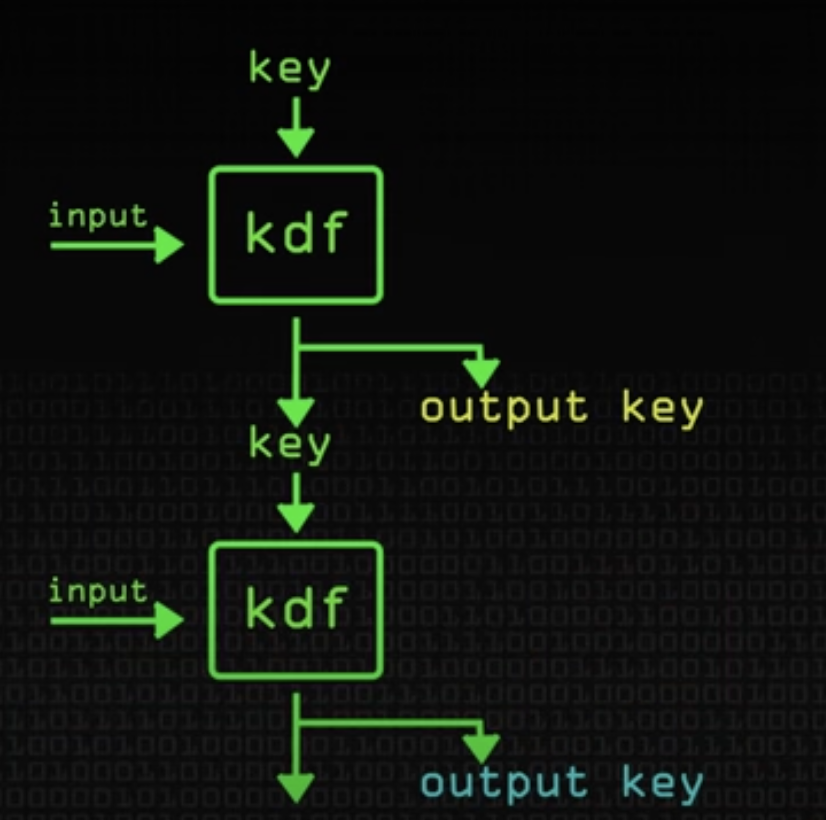
Double Ratchet
Message Encryption
Message Routing
Key Distribution
Authentication
User Management
Public Key Storage
Offline Messages
Initial key establishment between two parties using Signal Protocol specification:
KDF(DH1 || DH2 || DH3 || DH4)DH1 = DH(IK_A, SPK_B) // Identity × Signed PreKeyDH2 = DH(EK_A, IK_B) // Ephemeral × IdentityDH3 = DH(EK_A, SPK_B) // Ephemeral × Signed PreKeyDH4 = DH(EK_A, OPK_B) // Ephemeral × OneTime PreKey
Provides forward and backward secrecy with a new key for each message:
# Compile server javac ChatServer.java # Compile client javac ChatClient.java # Start server java -cp ".:lib/sqlite-jdbc-3.49.1.0.jar" ChatServer 9090 #or ./run.sh # Connect client java ChatClient <server_ip> 9090
# Direct end to end message @username Hello, this is a private message! # Broadcast end to end message broadcast Hello everyone! # Or just type for broadcast Hello everyone! # Exit application exit
This project demonstrates enterprise-grade security practices and modern cryptographic protocols. Check out the complete source code and technical documentation on GitHub.